Information Security and Quantum Cryptography
Maria Nenova
Description
Keywords: cryptographic protocols; information theory; quantum cryptography; quantum computing
H2020 challenge: Secure societies – protecting freedom and security of Europe and its citizens
Knowledge and skills (P: prerequisite; D: desirable, but not necessary): Communication protocols (P); Cryptography (P); Information theory (P); Analytical way of thinking (P); Cryptographic protocols (D); Quantum cryptography (D); Quantum computing (D); Programming abilities (D).
Security of information is one of the main tasks in our days. The desire for protection of health records, personal data, and communications is a great opportunity to advance the technology for that. One of the most effective and reliable ways to protect data spread through a communication media is the use cryptography. Classical crypto methods are symmetric and asymmetric ones. The PKI is also a developing area.
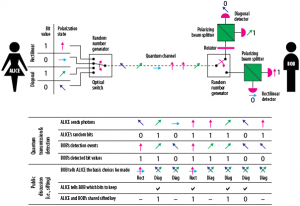
The next level of development in cryptography – quantum cryptography – is a big challenge for universities, researchers, technical labs (it started there), organizations and industry (lasers, equipment). This new area takes in a different level the protection of data. The basis is not a mathematical but all the idea is based on the specific feature of photons – the polarization.
Questions that need answers
Student teams will need to identify and provide more details about specific technologies which can be used within quantum cryptography:
- What are the main issues in the security of information from engineering point of view?
- What is the basis of cryptography, main challenges and algorithms to implement it?
- What models of a whole quantum cryptosystem (blocks and subsystems) exist?
- What is the technology behind the quantum cryptography?
- What equipment is needed to perform it?
- What are quantum cryptography protocols?
- What are quantum computers?
- What protocols are used in quantum computing?
- Which attacks and vulnerabilities against the cryptosystem and the cryptoprotocol exist?
- Technology used – prices and curent situation on the market for main parts of the quantum machines;
- Cost of the devices and elements for quantum computing and cryptosystems;
- Existing business models in the domain of cryptosystems.
- What will be the impact of such a big change in the cryptography system model?
- What will be the impact on the market, for example of computers?
- How can one enterprise for quantum computers or quantum cryptosystem components work?
- What will be the qualification of the people and working environment?
- What will hapen with the digital world taking into account described changes in the domain of cryptosystems?
Entrepreneurial Case Expert

Maria Nenova
TeamSoc21 Entrepreneurial Case Expert
Case study students (Group 1)

Iva Borisova
TeamSoc21 Valencia2019 Student

Maros Gonda
TeamSoc21 Valencia2019 Student

Valentin Patalau
TeamSoc21 Valencia2019 Student
Case study students (Group 2)

Alvaro Ravelo Medero
TeamSoc21 Valencia2019 Student

Blaz Jurisic
TeamSoc21 Valencia2019 Student

Iva Topolovac
TeamSoc21 Valencia2019 Student